
I Was Hacked – What I Did to Not Lose Everything
Table of Contents
No One Is Safe
I would like to say I am being dramatic but I am not, no one is safe from security compromise and losing access to their accounts, what we call hacked in today's words. There has been and will always be a war between protecting information and those who would use that information for malevolent purposes. Philosophical discussions on penetration testing and what drives someone to attempt breaching a system is not why I am writing about my experience. I'm not even a security expert but all you need is one incident to turn you in to someone deeply invested in protecting your information. Instead I am writing to highlight this simple fact;
Protecting your data from being hacked is a mutual responsibility. You are the owner and the user of your own data, your own online identity, you can allow other companies to use that information but you should be informed about the services you use, you should also hold companies accountable for a breach.
Box login from "Windows Chrome" Saturday, January 21, 2023
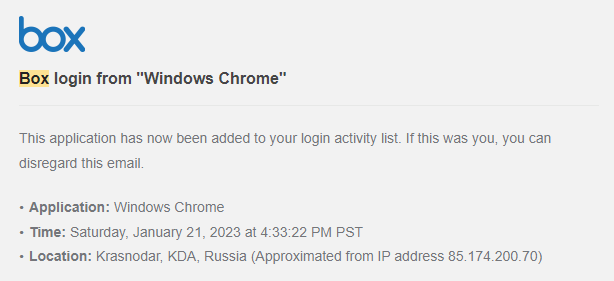
This email struck fear in to me when I received it because I don't use Box often. I certainly had not logged in to it when that notification came through, I was actually cooking dinner. Everything paused in that moment and I had to think, how could that have happened? The password I used for that account was generated, I don't know any passwords except my GMail and password manager passwords. It couldn't have came from either of those because I have two-factor authentication (2FA) enabled on both.
Then I remembered the email that came from LastPass in December. They had not one, but two security breaches in the last 90 days. That email linked to this article came during the typical flood of holiday emails when most users might just miss the notification. Not a fan of the timing of that notification given it could be missed.
That was the only potential ingress point because I thought I had nuked my LastPass vault when I moved to Bitwarden, obviously I was wrong.
I won't delve in to the breach, read the link and be informed but in short if you use LastPass, your entire encrypted vault was stolen, everyone's. The actor actually took the LastPass source code so they can try decrypting your passwords on a server separate from LastPass.
If you used LastPass or plan to continue using LastPass - Change your master password then change the passwords for all of your saved accounts.
Every single one of them is at risk.
What I Did To Not Lose Everything
Don't be lazy like I was, that is the truth of why my accounts became at risk and that is entirely on me.
When I test drove Bitwarden I stored it's password in my LastPass account because I wasn't sure that I wanted to migrate over. The problem is that my LastPass account was not nearly as secure as the accounts within it and that ultimately led to my personal breach. This is what I did to mitigate my exposure and if you use a password manger, I highly suggest you make similar modifications.
When I saw that notification I immediately did these things in this order to prevent further harm.
- Changed my password manager password
- Dumped my vault in to a CSV
- Nuked my vault so it was wiped clean
- Killed all existing sessions including my active one
- Changed passwords to my email accounts
- Changed passwords to my financial accounts and any government tied accounts
- Changed passwords to my social accounts
- Changed passwords to any accounts I knew were compromised
I left already compromised non-financial accounts alone to the end because they do not hold much value. Always prioritize your accounts so that you know what is ok to lose and what is not.
Security Measures To Live By
- Use a Passphrase It is good policy to use at a minimum a 24 character passphrase. This can be something silly or phenetic but do not make it something that is tied uniquely to you.
- Use Two-Factor Authentication This can be an authenticator app like Google Authenticator or Authy, even SMS but SMS is not the most secure due to SIM Swap Fraud.
- Increase Your Encryption Iterations When LastPass was first created their PBKDF2 iteration was ONE. Over time they have increase that but users who had a setting prior to the 'default' increase stay at that iteration level. You should at a minimum have 300,000 iterations. This means your passwords are hashed 300,000 times plus whatever your password manager uses. This makes it harder to brute force your password. I will write separate guides for increasing your iterations on LastPass and Bitwarden.
- Change Your Passwords When a Breach Occurs It used to be policy to change your passwords with some frequency but if you have good passphrase then this is not necessary unless you feel that your account is compromised. Always change your password when there is a service you used that has had a security breach.
Take your online account security seriously, be informed, have a plan of attack if you get compromised or feel that you have been hacked. It takes almost 200 days before a breach is identified on average. For single users this can be years instead. Do not be a victim, take measures to prevent it.
Did you enjoy this content?
If so please let me know so that I know what you enjoy reading.
If you enjoyed this content, please consider subscribing to get future updates!

